
Wind River says the singular architecture of its Helix Virtualization Platform for running embedded systems is more secure from cyber attack than the alternative of running each embedded system independently. EASA and FAA cybersecurity mandates are likely to ramp up in the next two years. Photo: Wind River
Aviation cybersecurity mandates by the European Union Aviation Safety Agency (EASA) and the Federal Aviation Administration (FAA) are coming in the next two years, according to participants in an Avionics International Apr. 7 webinar, Clearing the Skies of Cybersecurity Vulnerabilities from the Ground Up, .
This year, EASA may adopt AMC 20-42 (NPA 2019-1) that will link information security guidelines to the high-level cyber standards of RTCA DO-326A or the EUROCAE ED-202 series.
Asked during the webinar how the avionics industry has thus far embraced airworthiness cybersecurity standards in RTCA DO-326A, 355 and 356, Alex Wilson, the director of aerospace and defense at Wind River, said that cybersecurity standards "have been adopted slowly, but I think we'll see a more rapid adoption throughout this year and the coming year."
"Currently, the standards are more voluntary or applied on a case by case basis on aircraft systems as they go into certification," he said. "These standards have been around in embryonic form since the [Boeing] 787 [Dreamliner] first went through its airworthiness process [a decade ago]."
Wilson predicted that "once we see those standards being mandated through rules and regulations, we'll start to see a massive adoption and a requirement of all new avionics systems to go through [these] standards."
Such mandates may spark, or re-ignite, the operational red teaming of aircraft cyber systems.
It has been unclear what the path forward is for cyber vulnerability testing of airliners in the United States after last month's decision by the Department of Homeland Security's (DHS) Cybersecurity and Infrastructure Security Agency (CISA) to end the testing of a Boeing 757-200 at the Federal Aviation Administration (FAA) William J. Hughes Technical Center in Atlantic City.
Cyber vulnerabilities are not the exclusive domain of commercial airliners, but also are faced by military and business aircraft and future urban air mobility platforms and by diverse systems, such as onboard radar altimeters, Global Positioning System receivers, and military Identification Friend or Foe (IFF) systems.
Paul Hart, the chief technology officer at Curtiss-Wright Defense Solutions, said that combat search and rescue helicopters can have up to 60 computers onboard to run flight control processes, such as take-off and landing, and complex synthetic vision systems, while UAVs normally have less than 10 processors for flight control and detect and avoid systems, and airliners "typically have more than 100 computing platforms."
While e-Enabled aircraft provide flight and cost advantages for operators, they also come with cybersecurity vulnerabilities.
"The obvious question is, 'Isn't it just safer to separate from the Internet?'" Wilson asked at the start of his webinar presentation. "Why should we e-Enable and connect our aircraft? There's a whole list of reasons why we might want to do that. In this modern age, everyone is going through a process of digital transformation, moving to more intelligent platforms, and that gives us huge benefits in terms of operational efficiency, the ability to implement new advanced technologies, such as predictive maintenance so that we can reduce operational costs of our aircraft systems and allow us to update more efficiently the aircraft systems themselves, such as weather data on the aircraft and other data sources."
"That also allows us to increase the amount of revenue we're getting from our passenger systems and provide a better passenger experience while we fly," Wilson said. "There are huge challenges when we look at aviation systems that are very different to those we see in the IT world. Within the IT world we tend to see applications moving to the Cloud-based systems and moving very quickly with new updates daily and new features and functionality. The security standards within the IT world are certainly not well suited to the aviation world so we need to think about how we manage that. Also, within the IT world we tend to see systems being updated very rapidly compared to the update cycle that we see within our aircraft. So there are lots of challenges as we start to connect and provide that Internet connectivity."
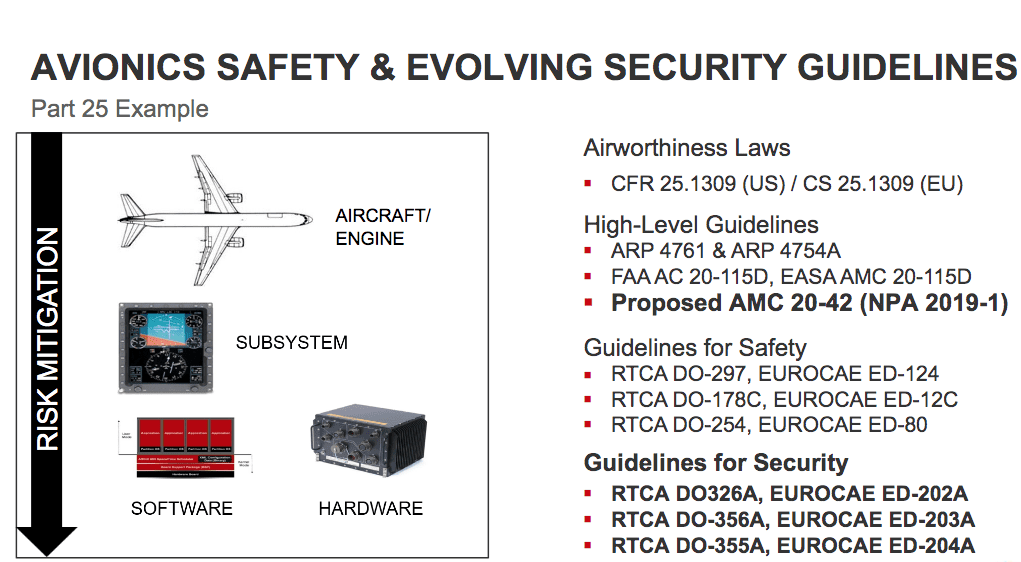
These are the guidelines for cybersecurity associated with connected aircraft systems, which as of today, are not mandated by civil aviation authorities. Photo: Wind River
Indeed, while relatively isolated ACARS and VHF video data links and, more recently ADS-B (In) and ADS-B (Out) were the major features of aircraft electronics, aircraft wireless connectivity has opened up a range of vulnerabilities, Hart said. Instead of leather flight bags with paper charts, aircrews now can carry aboard Electronic Flight Bag (EFB) tablets and iPads that are able, through aircraft Wi-Fi, to obtain flight parameters to calculate take-off performance, for example. Maintenance engineers can also connect wirelessly to avionics systems of flight line aircraft through laptop Portable Maintenance Aids (PMA) for troubleshooting aircraft systems.
To update its cybersecurity policy as new threats emerge, Wind River uses the CIA Triad technique, which maps requirements against the three pillars of cybersecurity: Confidentiality, sustaining data the privacy of data being transmitted and stored, such as map data; Integrity--the accuracy of data during and after software updates, for example; and Availability for the uninterrupted flow of data, even in the face of common denial of service cyber attacks.
 |
Want to hear more on aircraft connectivity applications? Check out the Global Connected Aircraft Podcast, where Avionics editor-in-chief Woodrow Bellamy III interviews airlines and industry influencers on how they're applying connectivity solutions. |
Michael Mehlberg, vice president of marketing at Star Lab, a Wind River subsidiary, said that Wind River has adopted a cybersecurity first holistic approach through an examination of how cyber components interact with one another and a "defense in depth" with layers of cyber protection. Linux-based embedded systems, for example, while flexible, also have vulnerabilities, which Wind River mitigates through such means as operating system-level hardening, Linux LSM (Security-Enhanced Linux stacking), immutable deployment configurations, and multiple file systems, such as the authentication and/or encryption of applications, libraries, and data.
In addition, a secure boot process is a "massively important part of the cybersecurity process" to ensure no cyber intrusion happens while computer systems are at rest.
"The security policy and configuration really has to be a combination of products, product features, advanced security features, professional services to provide and mitigate a security assessment and add additional security where required and a combination of partnerships, for instance the Curtiss-Wright hardware with the Wind River software, in order to implement a secure system," Wilson said
