Norsk Hydro, a major global aluminum producer that is also Norway's third-largest producer of hydropower, has been stricken by an extensive cyberattack–reportedly ransomware–that forced its entire global network offline.
The company powers its sizable aluminum production operations with 20 hydropower plants concentrated in Telemark, Røldal-Suldal, Sogn, and Vennesla, producing a total 10 TWh per year. It told POWER on March 19 that its power operations were not impacted.
Its bauxite and alumina production, and primary metal plants were also operating as usual, though some with a "higher degree of manual operations." The segment that is most affected is Hydro's extruded solutions and rolled products, which show a "lack of ability to connect to the production systems," causing "production challenges and temporary stoppage at several plants," it said.
The company disclosed the attack in line with Norwegian securities law. It said the incident began in the early hours on Tuesday. "IT-systems in most business areas are impacted and Hydro is switching to manual operations as far as possible," Norsk Hydro reported at 3:31 a.m. EST. "Hydro is working to contain and neutralize the attack, but does not yet know the full extent of the situation."
In a 9:41 EST update, the company said it had isolated all plants and operations and was switching to manual operations and procedures "as far as possible." Its main priority was to ensure safe operations, and limit operational and financial impact, and the event had not led to any safety-related incidents, it said. However, the company noted it did not "yet know the full extent of the situation," noting it was "too early to indicate the operational and financial impact, as well as timing to resolve the situation." For now, it said, "Relevant authorities have been notified and are supporting Hydro in the efforts to resolve the problem."
A Possible Ransomware Attack
In the hours following first reports of the attack, NorCERT, Norway's national computer emergency response team and cybersecurity center, reportedly issued a notification that said Norsk Hydro was one of an unspecified number of victims affected by LockerGoga ransomware. "The attack was combined with an attack on Active Directory (AD)," the alert, which was first reported by Norwegian state-owned media NRK, said. NorCERT urged all public enterprises in Norway to be vigilant for further spread of the ransomware virus.
The relatively new strand of ransomware gained prominence after a cybersecurity attack that infiltrated systems at French engineering consultancy firm Altran Technologies on January 24, according to information security and technology news publication Bleeping Computer.
However, ransomware has been an enduring worry for industrial control system (ICS) security, owing in large part to devastating effects of wormable malware such as WannaCry, NotPetya, and BadRabbit. In 2017, NotPetya ransomware reportedly caused $300 million in losses and prompted large logistics firm Maersk to wipe and reinstall 4,000 new servers, 45,000 new computers, and 2,500 applications to restore operations.
ICS cybersecurity firm Dragos in February warned that commodity malware and wormable ransomware continued to pose significant risks. Last August, it noted, an operational error during a software installation at Taiwan Semiconductor Manufacturing Co. caused a WannaCry infection that affected more than 10,000 machines, leading to a financial impact of at least $250 million.
"We anticipate increased risk of operational losses due to incidental malware infections in ICS environments; the results of mishaps during initial intrusion and reconnaissance operations within the [operational technology] realm; and new disruptive attacks based on the results of increasing research and reconnaissance activity," Dragos said in a white paper assessing ICS activity groups and the threat landscape over 2018.
Inside the LockerGoga Crypt
According to Andrea Carcano, co-founder and chief product officer with Nozomi Networks, a firm that performs real-time ICS monitoring, a notable aspect of the Norsk Hydro cyberattack is the company's laudable incident response. Though the company's website is still down as of noon EST on March 19, "They made a live stream with a brief on the attack and they're keeping all informed using their Facebook channel," he told POWER on Tuesday.
LockerGoga, like other ransomware, seeks to hold data ransom, he noted, but it is especially insidious because it is able to encrypt files that have the following extensions: doc, dot, wbk, docx, dotx, docb, xlm, xlsx, xltx, xlsb, xlw, ppt, pot, pps, pptx, potx, ppsx, sldx, pdf. "The extension types are an indicator that the main goal of the threat actor is to encrypt files containing important data for the users," he said. A user would know they've been infected because the targeted files would be encrypted and the extension ".locked" would be attached to the end of the filenames, he explained.
Carcano also said that at the end of the encryption phase, attackers dropped a "README-NOW.txt" file inside the filesystem. It contains the following message, which essentially extorts users to pay a ransom using Bitcoin cryptocurrency if they want their files back:
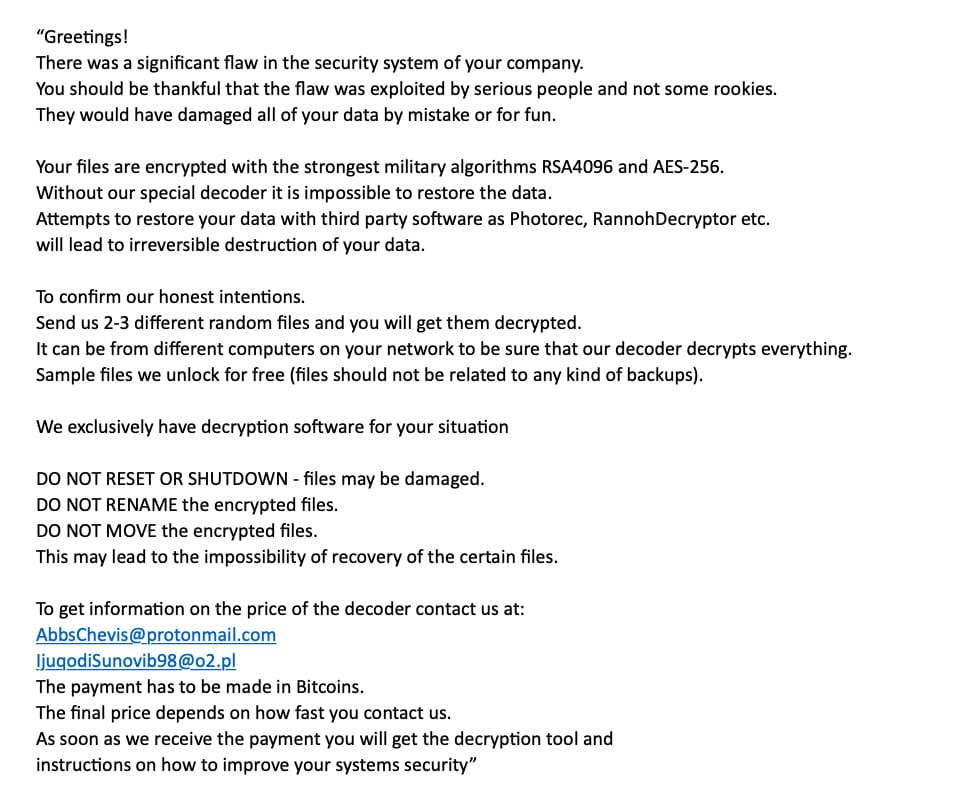
LockerGoga ransom note as dropped in a "README-NOW.txt" file inside the filesystem. Courtesy: Nozomi Networks
Notably, "The malware is not able to spread itself to other targets. It seems to implement some anti-analysis techniques in order to hide itself from analysts; for example, it seems to detect the presence of a Virtual Machine and have the capability to delete itself from the filesystem trying to avoid the sample collection," Carcano explained. "Considering the fact that the attackers were not interested in adding custom and complex capabilities (C&C, DNS beaconing, etc.) we can assume the scope was merely disruptive and did not have an espionage intent."
He also pointed out that some research suggests, and NorCERT confirmed–but it remains unconfirmed by Nozomi Networks Labs–that the attackers could have used Active Directory as a mechanism for spreading the malware. That raised a possible scenario of "an attacker that was already able to infect a targeted system registered in the Domain Admin Group could have placed the malicious executable in the Netlogon directory so that could be automatically propagated to every Domain Controller," he said, noting that many firewalls accept the Active Directory by default.
According to Tyler Moffitt, security analyst at internet security firm Webroot, another notable aspect of LockerGoga is that its encryption process is "slow." That's "because it creates a new process each time it encrypts a new file and also exhibits no detection evasion techniques, showing a lack of sophistication," he said. Moffitt also noted LockerGoga was signed using a valid digital certificate, which has since been revoked. "We have been protecting our customers from LockerGoga since we first encountered it January 14th and do expect it to become a big player in the ransomware scene, but will monitor its progress," he told POWER in a statement on Tuesday.
A Realm of Vulnerable Targets
As more details about the Norsk Hydro attack emerge, a number of ICS cybersecurity experts noted the incident spurred alarms about how vulnerable critical infrastructure can be to ransomware.
"Manufacturing companies are an obvious target for ransomware because downtime is measured in millions of dollars per day–so as you might expect, CEOs are eager to pay," Phil Neray, vice president of Industrial Cybersecurity at Boston-based IIOT and ICS security firm CyberX, told POWER. "Plus the security of industrial networks has been neglected for years, so malware spreads quickly from infected employee computers in a single office to manufacturing plants in all other countries." Neray noted these attacks are especially serious for metal or chemical manufacturers "because of the risk of serious safety and environmental incidents, and the bottom-line impact from spoilage of in-process materials and clean-up costs."
However, Barak Perelman, CEO of ICS security firm Indegy, on Tuesday told POWER that at this early stage, there was no indication that Norsk Hydro had been specifically targeted. "It is safe to assume that this was a generic ransomware type of attack similar to Wannacry," he said. "It appears that the initial attack began on the IT network and quickly propagated to the [operational technology (OT)] side of the house, which forced production to be taken offline."
But Perelman–and other ICS security experts–stressed that the incident illustrates the risks associated with connecting industrial control system environments to IT networks and/or the internet. "The two main problems have to do with patching and recovery of OT systems," he explained.
"Many ICS devices are end of life, so vendors do not issue patches for them. Therefore, they cannot be patched against known vulnerabilities. Second, many operators have not invested in security and monitoring tools. This makes it difficult to detect attacks until it's too late. Meanwhile, restoring ICS systems from backups is often not possible since logs and back-ups don't exist. Without tools that provide visibility and security controls across both IT and OT environments, nuisance attacks like this one are difficult to defend against and can cause material damages to operations," he said.
Nozomi Networks' Carcano also noted the attack offered a stark reminder that security requirements are constantly changing as industrial organizations continue to modernize and introduce internet-enabled technology into plants.
"While these new digital processes can offer significant benefits to industrial organizations, they also provide new opportunities for attackers, as potential entry-points into networks," he said. "As industrial organizations automate and digitize plant floors, the security of these new processes must be forethought to reduce the risks of potential attacks."
–Sonal Patel is a POWER associate editor (@sonalcpatel, @POWERmagazine)
