As digitalization becomes more common and remote operations become necessary, guarding against cybersecurity breaches grows even more critical
The hacking of a Florida water plant, which made headlines in February, was a poignant reminder of the dangers posed by breaches of cybersecurity. Although the incident was discovered before real harm could occur, it highlights the importance of due vigilance when it comes to the security of IT (information technology) and OT (operational technology) of plants in the chemical process industries (CPI).
Threats are always there
"The [CPI] face increasing and more sophisticated cybersecurity threats," says Michael Lester, director of cybersecurity strategy, governance and architecture at Emerson (St. Louis, Mo.; www.emerson.com). "Attacks are constantly evolving, as commoditized malware and advanced technologies provide new capabilities to threat actors. The motivation is still mostly financial gain, but nation state actors are increasingly involved and there are increasing numbers of attacks targeting the industrial control space from various threat actors," he says.
"Smaller chemical facilities often have older ‘patchwork' automation systems that increases vulnerability compounded by a lack of resources to routinely assess and strengthen their cybersecurity," Lester says. "Recent attacks are a reminder that regardless of size, industry or location, all facilities need to be aggressive about cybersecurity."
"Cyber-threats to industrial organizations will continue to increase, in both volume and sophistication," echoes Donovan Tindill, senior cybersecurity strategist at Honeywell Process Solutions (Houston; www.honeywellprocess.com). "We've reached a point where cyberattacks are not a question of if, but rather of when and what could be done to prevent that attack or minimize its harm. If you own or manage an OT-based operation, the time to take action and prepare your network is now," he says.
IIoT increases vulnerability
Maintaining a competitive edge means leveraging the industrial internet of things (IIoT) technologies, says Emerson's Lester. "More connections mean more potential vulnerabilities – and organizations need to prioritize cybersecurity equally alongside their IIoT and digital transformation initiatives," he says.
Honeywell's Tindill would agree. "The growth in the number of sensors or cloud connectivity increases the scope of cybersecurity, the attack footprint and the exposure as the number of cyber assets requiring cybersecurity protection and detection increases," says Tindill. "The objective of robust cybersecurity management is to protect the increasing count of cyber assets with basic cyber hygiene, such as strong remote access, electronic security perimeter, patching, monitoring, and incident response to ensure it is not more vulnerable," he says.
"In our experience, it is necessary to audit cybersecurity at least once per year and remediate all risks that exceed the tolerance level for that organization," continues Tindill. "Recommendations may include additional network segmentation, application whitelisting, endpoint hardening, security logging, proactive monitoring, robust incident response, and more," he says.
The benefits of due vigilance are real. "If you implement a foundational set of security controls in your plant systems that everyone should have, like patching, endpoint protection, backups and inventory management, then you can reduce your cybersecurity risk by up to 85%," says Ben Dickinson, global product manager – cybersecurity, ABB Energy Industries (Zurich, Switzerland; www.abb.com).
"The proliferation of IIoT devices introduces a new risk that companies must consider as they have the potential to increase the attack surface that hackers can exploit," says Mark Carrigan, chief operating officer, PAS Global, LLC (Houston; www.pas.com; Figure 1). "The reality today is that in most areas, OT cybersecurity trails IT cybersecurity. Many companies are realizing that they must implement the basics of cybersecurity for their OT assets, including collecting a holistic inventory of all assets (hardware, software and firmware), identifying and remediating vulnerabilities and improving the backup and recovery processes to ensure they can minimize the impact of a successful attack," says Carrigan.
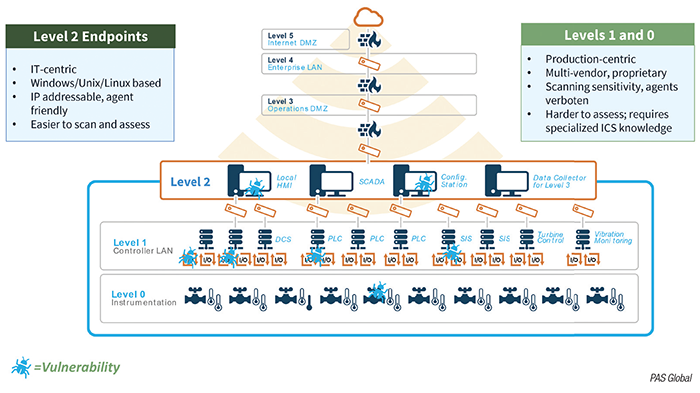
Figure 1. Discovering and remediating vulnerabilities in OT is complex
To help in these efforts, PAS offers its Cyber Integrity platform (which includes Automation Integrity) to prevent, detect and remediate industrial cyberthreats. PAS Cyber Integrity is said to deliver comprehensive inventory, vulnerability, configuration, compliance, backup and recovery, and risk management for OT assets. In January, PAS launched a new module for Automation Integrity – Sensor Data Integrity – that "improves the discovery and configuration-management of IIoT devices that are prevalent in the process industries," says Carrigan.
Sensor Data Integrity enables industrial organizations to ensure configuration-data integrity for smart and traditional sensors with signal tracing and validation. This addition to Automation Integrity helps reduce both process safety and cyber risk in support of digital transformation initiatives. The new Sensor Data Integrity module provides multi-vendor discovery of smart IIoT and traditional analog sensors; visibility to the complete inventory and potential cyber vulnerability for sensors; creation of templates to define approved configuration for each sensor type; automated detection of configuration errors; automated identification of devices that don't match assigned templates; cross-checking of parameters; support for large-scale, multi-site sensor deployments; and sensor signal tracing, validation and visualization. The information provided by Sensor Data Integrity can also be leveraged by sensor asset-management systems (AMS) to support instrument calibration, and can feed PAS Cyber Integrity to support cybersecurity vulnerability assessments.
Security monitoring
Digital transformation typically involves providing more people and more access to data from the industrial control system (ICS) and other OT devices and systems, says Emerson's Lester. "This may include not only manufacturing and production staff members, but also third-party suppliers who assist in optimizing asset and overall performance. This increased data flow requires careful consideration of the architecture and systems and processes to continually monitor this architecture," he says.
"Security monitoring is not only an important mechanism to detect threats, but also helps with forensics and preventing similar future attacks," Lester continues. "A centralized Security Information and Event Management (SIEM) platform can take ICS workstations, servers and network equipment system events and logs and put them into a meaningful dashboard for prompt response from qualified resources. A SIEM can also monitor network traffic data through Network Security Monitoring appliances using a one-way-only communication flow as an added security monitoring feature," he says.
At the forefront of such efforts, LogPoint A/S (Copenhagen, Denmark; www.logpoint.com) launched Version 6.10 of its SIEM solution in February. This latest LogPoint release enables sharing of security analytics and dashboards and provides more context on attack developments supporting the latest MITRE ATT&CK framework. LogPoint 6.10 also integrates with third-party detection-and-response systems to send notifications to Managed Detection and Response (MDR) providers.
Role-based access to dashboards in LogPoint 6.10 helps teams effectively manage and update each other on evolving threats, increasing efficiency in the SOC and decreasing false positives. Configurable role-based, read-write access to each dashboard means that whenever an analyst makes an update, all users with access to the dashboard see the changes, says the company.
Security in the time of pandemic
"The biggest trend over the past year has been remote work as a solution to mitigate the spread of COVID-19," says Matt Malone, Industrial Control system (ICS) Cybersecurity Consultant, Yokogawa Corp. of America (Sugar Land, Tex.; www.yokogawa.com/us). "In our case, it greatly expanded interest in an existing product portfolio of ours, secure remote services. For example, our VPS Remote application (Figure 2) provides access to users of our Centum VP distributed control system from virtually any location. It has provided many of our clients the means to continue working in spite of COVID-19 without sacrificing safety or security. COVID-19 has also accelerated digital transformation in the industry; now, companies are realizing that cybersecurity is a prerequisite to successfully transforming."
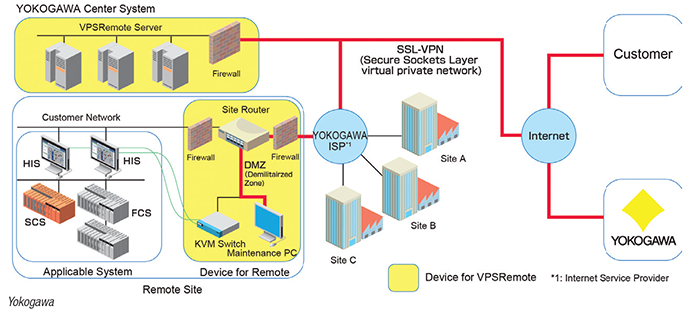
Figure 2. The VPSRemote is configured with devices installed at the user's site for remote operation and linked to the secure Yokogawa Center System, which provides a safe network communication environment to connect these devices and systems
"While our secure remote services portfolio had already been on the market leading up to the COVID-19 outbreak, Yokogawa has since launched an entirely-new cybersecurity management solution that bridges IT and OT," says Malone. It is not solely based on technology but brings in numerous, management best practices, he adds.
For instance, companies can invest in general cybersecurity awareness programs for IT, OT and hybrid IT/OT personnel, explains Malone. They can perform security assessments or audits of control systems and control-system networks and increase visibility of control system cyber assets and configurations. They can implement anomaly and intrusion detection tools on control-system networks and invest in cybersecurity education and training for IT, OT and hybrid IT/OT personnel, says Malone.
"Throughout the COVID-19 pandemic, Emerson has worked with customers to provide secure remote services," says Lester. "Leveraging a variety of IIoT technologies and expertise we have enabled services such as non-intrusive health monitoring of valves, equipment performance monitoring and control system health monitoring to meet their operational needs. Secure distributed cloud-based engineering environments have also supported customers with virtual factory acceptance testing (FAT) to ensure projects remain on schedule," Lester says.
"An increased requirement to operate and maintain plants remotely over the last year has led to new initiatives that ensure remote access is carried out securely," says ABB's Dickinson. "Many of the vulnerabilities exploited by attackers relate to insecure remote access setup, so it's important that an appropriate level of security is embedded in your digital and remote-access solutions," he cautions.
Other product developments
ABB has developed a Secure Reference Architecture (Figure 3) and Cyber Security Risk Assessment Service, both based on IEC 62443, that couples together best practice approaches to securing industrial distributed control systems (DCS). "We work strategically with our customers to identify both their risk exposure and assess the maturity of their system security and security management practices. This enables the identification of appropriate security levels required for each system in order to mitigate cyber security risk to an acceptable level that corresponds to the organization's risk appetite and regulatory compliance requirements," explains Dickinson.
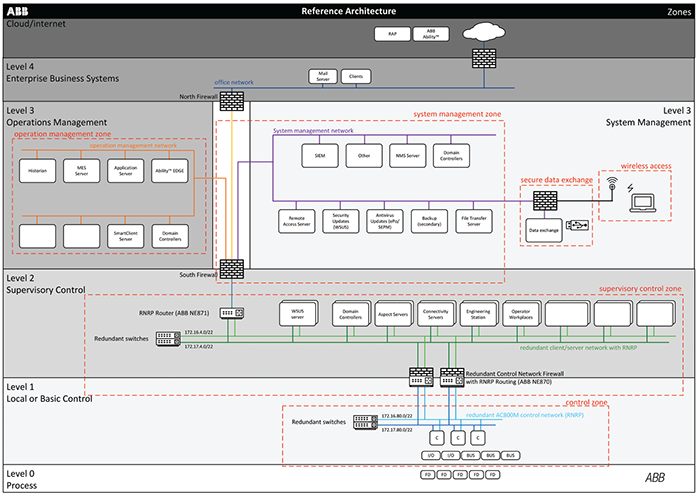
Figure 3. The Reference Architecture harnesses ABB's domain expertise in both cybersecurity and control-system technology to define a standardized definition of a secure control system architecture, and using a standard terminology that aligns with international standard IEC62443. This enables ABB to standardize the way in which it designs and implements its control-systems technology to deliver a secure setup by default and using a consistent approach across different delivery teams
This approach ensures optimal return on investment of cybersecurity improvement programs by ensuring all investments are tied to risk, Dickinson continues. Implementing the recommended security controls to achieve the identified security level will significantly reduce risk, but not eliminate it completely. "To address the residual risk, ABB has developed an event-monitoring service to help our customers effectively monitor their control systems and detect when an attacker has been successful in targeting your systems in order to respond quickly and effectively and thus limit the damage they have on a system," he says.
Meanwhile, Honeywell continues to invest in OT cybersecurity products and services, says Tindill. Some recent new offerings include Honeywell Forge Managed Security Services with Advanced Monitoring & Incident Response. Scheduled to be launched at the end of March, this offering is configured especially for OT environments. "This 24/7-managed security service combines automated analytics with the know-how of certified cybersecurity professionals to help identify, mitigate and manage cybersecurity threats," says Tindill.
Other recent offerings include Honeywell Forge Cybersecurity Suite, the latest release of industry proven software that helps users better manage the operations of OT-centric cybersecurity with improved asset discovery, risk and compliance monitoring and more. Also recently introduced is PCN Hardening Services. "Configured especially for OT networks, this service offers a method of better securing process control systems and network devices by applying elevated security configurations to existing components," says Tindill.
