Cybersecurity threats are outpacing the energy sector's "best defenses," and costs of preventing and responding to cyber incidents are straining company efforts to protect critical infrastructure, the Department of Energy (DOE) warned as it released a comprehensive five-year cybersecurity strategy for the industry.
The Multiyear Plan for Energy Sector Cybersecurity, dated March 2018 but which was made public by the DOE's Office of Electricity Delivery and Energy Reliability (OE) on May 14, lays out an "integrated strategy" for the DOE's new Office of Cybersecurity, Energy Security, and Emergency Response (CESER). It essentially seeks to "gain an upper hand" in the fight against cybersecurity, outlining "disruptive changes in cyber risk management practices."
Power companies and utilities, along with oil and gas entities, have integrated advanced digital technologies to automate and control physical functions for improved efficiency and adjust to a "rapidly changing generation mix," but this has created a "larger cyber attack surface and new opportunities for malicious cyber threats," the plan notes.
"Nation-states, criminals, and terrorists regularly probe energy systems to actively exploit cyber vulnerabilities in order to compromise, disrupt, or destroy energy systems. Growing interdependence among the nation's energy systems increases the risk that disruptions might cascade across organizational and geographic boundaries," it adds. Though government and the private sector have continually increased spending on cybersecurity operations and maintenance (O&M), "it has become increasingly difficult for energy companies to keep up with growing and aggressive cyber attacks."
Costs to defend against or respond to growing threats and incidents have surged and continue to grow more expensive each year, the DOE noted. A 2015 study by the Ponemon Institute, for example, estimates the annualized cost of cyber crime for an average energy company to be more than $27 million. The DOE also cited a 2014 report from the Newton-Evans Research Co. that claims control system security costs for the electric transmission and distribution equipment market range from roughly $150 million to as much as $800 million. "Simply put, the cost of preventing and responding to cyber incidents in the energy sector is straining the ability of companies to adequately protect their critical cyber systems," the DOE warned.
A Comprehensive Strategy that Considers Industry and Research Contributions
The strategy has three goals: to strengthen current energy delivery systems through information-sharing and situational awareness; to coordinate cyber incident response and recovery; and to develop "game-changing solutions" through research and development to create more secure and resilient energy systems in now and in the future.
The DOE says it has a "robust portfolio of dozens of targeted activities and research development and demonstration (RD&D) projects now underway to achieve the broad goals and objectives." Here are some examples described in the plan:
CRISP. The cybersecurity risk information sharing program (CRISP) is designed to allow energy sector owners and operators to voluntarily share cyber threat data in near-real-time, and analyze this data using U.S. intelligence, and receive machine-to-machine threat alerts and mitigation measures. The measure is managed by the Electricity Information Sharing and Analysis Center (E-ISAC), but it should eventually be owned and operated by the private sector. Currently, CRISP is comprised of 26 participating utilities, which account for 75% of U.S. electricity customers. By fiscal year 2021, the DOE hopes that 100 utilities will be using CRISP (and that the cost of using CRISP will fall by 50%). Participants will advance the program's analysis capabilities through the OE's Cyber Analytics Tools and Techniques (CATT) project, as well as through sharing of threat indicators in operational technology (OT) systems by piloting a real-time OT data sharing and analysis with four utilities in OE's Cybersecurity for the OT Environment (CYOTE) project.
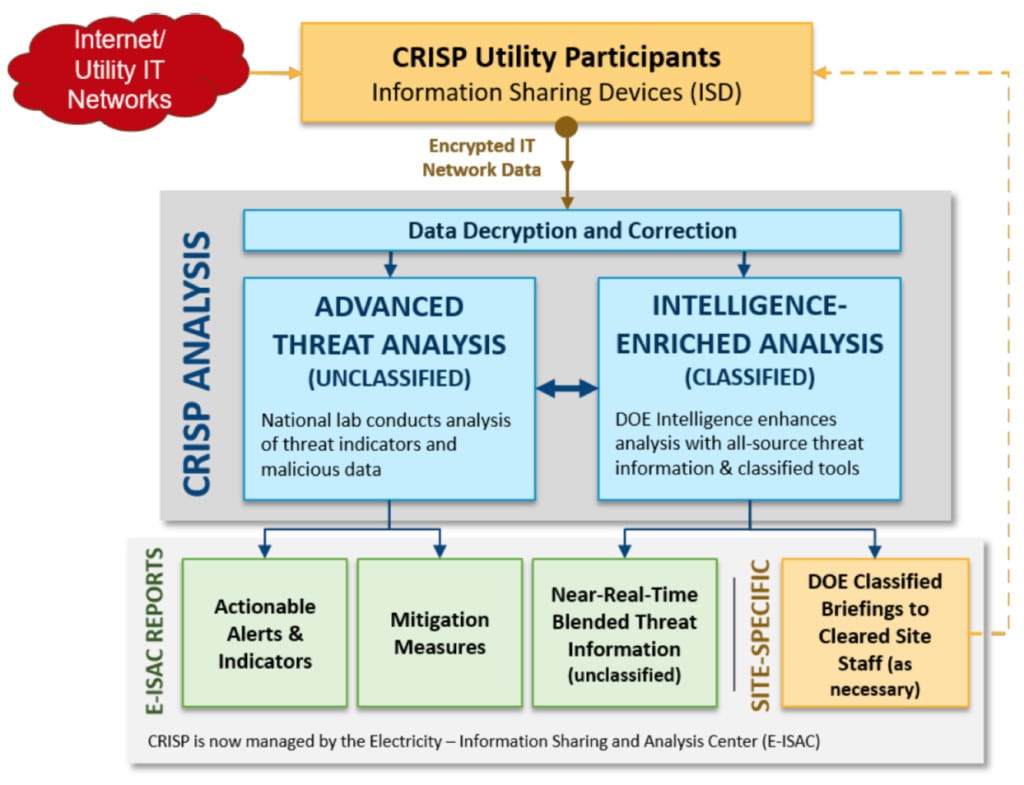
How CRISP analysis works. The DOE reports that 26 utilities currently participate in the cybersecurity risk information sharing program (CRISP). The agency wants to expand energy sector participation to 100 utilities by 2021. CRISP participating companies essentially install an information-sharing device (ISD) on their network border, just outside the corporate firewall. "The ISD collects data and sends the data in encrypted form to the CRISP Analysis Center. The Center analyzes the data it receives and, using government-furnished information, sends alerts and mitigation measures back to the participating companies about potential malicious activity. These alerts can be pulled directly into the companies' intrusion detection or intrusion prevention systems," says the DOE. Source: "DOE Multiyear Plan for Energy Sector Cybersecurity," March 2018
The DOE reports that 26 utilities currently participate in the cybersecurity risk information sharing program (CRISP). The agency wants to expand energy sector participation. CRISP participating companies essentially install an information-sharing device (ISD) on their network border, just outside the corporate firewall. "The ISD collects data and sends the data in encrypted form to the CRISP Analysis Center. The Center analyzes the data it receives and, using government-furnished information, sends alerts and mitigation measures back to the participating companies about potential malicious activity. These alerts can be pulled directly into the companies' intrusion detection or intrusion prevention systems," says the DOE.
OT Capabilities.Among notable objectives is that the DOE wants by 2019 to develop an OT sensor device that is capable of monitoring specific OT/industrial control system (ICS) data streams. By 2020, it expects "wide-scale energy sector implementation of the OT sensor and CRISP integration."
Mutual Assistance. OE is meanwhile working with the DOE's national laboratories to develop an "integrated mix of specialized cyber resources and capabilities that can be deployed during a cyber incident to help energy companies identify and respond to a cyber attack." The DOE is currently required to provide cyber-specific technical expertise and assistance to back energy sector response during a cyber incident and restore or maintain critical functions, the agency noted.
Confronting Cyber Risk Through Technology
The plan also describes several technology pathways to help prevent, detect, and mitigate cyber incidents:
An Eye on Prevention. According to the DOE, San Diego-startup Qubitekk, which works to commercialize technology to speed up adoption of quantum computing and cryptography technologies and applications, is leading a research partnership that will use quantum key distribution (QKD) to slash the cyberattack surface. QKD essentially enables the secure exchange of cryptographic keys to prevent compromise of critical energy sector data and detects attempted eavesdropping in real-time.
Iowa State, meanwhile, is leading a research partnership to develop algorithms that continuously–and autonomously–assess and slash the cyberattack surface across the energy delivery system (EDS) architecture, including at substations, control centers, and SCADA networks.
Detection and Identification of Cyber Incidents.The National Rural Electric Cooperative Association (NRECA)is heading up a research partnership to develop technology that will quickly identify anomalies in utility control communications. Those anomalies could eventually serve as indicators of a cyber compromise and help other utilities expedite mitigation.
Schweitzer Engineering Laboratories (SEL), on the other hand, is heading up a research partnership to detect and spoof the precise, synchronized GPS time signals typically used for synchrophasordata. That measure could help provide "unprecedented visibility" of grid operations across wide geographic regions. It could also develop potential mitigations, such as shifting to an alternative precise timing source. Texas A&M University is also developing algorithms to detect the compromise of precise synchronized timing signals throughout the grid architecture.
Automated Defense for High-Voltage DC Systems. Zurich-based technology firm ABB is leading a research partnership to enable high-voltage DC systems to detect and automatically reject commands that could destabilize the grid, the DOE said. "Using the physics of the grid, the capability will anticipate how the grid would react to a received command–rejecting commands that would jeopardize grid stability while executing legitimate commands in time," it explained. The project builds on a prior OE RD&D project, which the DOE said had successfully demonstrated the capability in transmission-level AC systems.
Model Risk Assessments. At the same time, the Cyber Resilient Energy Delivery Consortium (CREDC), which the University of Illinois at Urbana-Champaign is spearheading along with nine other universities as well as two national laboratories, will formally model risk assessment and network diversity to assess the resilience of EDS against zero-day attacks. The risk assessment model can be used to classify attacks based on potential impacts and select a resilient mitigation approach.
Industry-Led Efforts Are Promising
Industry is also stepping up efforts to protect grid systems. Examples of projects industry-led OE projects are:
Grid-Edge Devices.Intel is leading a research partnership that could help secure the cyber interaction of grid-edge devices with the cloud. The measure is important as more efficient and economical grid operations are expected from future architectures that increasingly use the cloud for "big data" analytics to process new data streams from an increasing number of grid-edge devices, the DOE noted.
Dynamic Load Management. Anticipating more dynamic load management in the future, the United Technologies Research Center is leading a research partnership that will allow building management systems that interact with the building's energy provider to recognize a cyber incident that could impact the grid, and switch to a more secure platform that may have limited functionality but is better able to survive the incident.
Protection of Linked Microgrid Systems. In tandem, ABB is also developing a cyber-physical control and protection architecture for the secure integration of multi-microgrid systems, enabling stable performance during a cyberattack. Future grid architectures may rely on microgrids, and systems of microgrids, for increased grid reliability, allowing for the creation of intentional electrical islands when this could benefit grid operations.
Several Shortcomings Still Need to Be Addressed
According to the plan released Monday, collaboration between the government, national laboratories, universities, equipment vendors, and energy operators has grown in strength significantly. However, an assessment undertaken by seven national laboratories to understand the energy sector's progress toward strategies and milestones outlined in the DOE's 2011 Roadmap to Achieve Energy Delivery Systems Cybersecurity highlights that sector-wide impact of new tools and technology advancement was generally limited by a lack of awareness. "Outreach was a key barrier to wider adoption of cybersecurity tools or participation in partnership activities," it says.
Among some concerns it notes were that federally funded resources and tools like the Cybersecurity Capability Maturity Models (C2M2)–a mechanism designed to help organizations evaluate, prioritize, and improve cybersecurity capabilities with a set of industry best practices–or procurement language that purchasers and suppliers can use as a starting point to discuss necessary cybersecurity measures during the EDS process–are valuable but haven't been adopted widely in the power space. Also, guidelines may not be appropriately scaled for small utilities. In contrast, the oil and gas industry has nearly universally implemented best practices, it says.
As significantly, information sharing–through the Department of Homeland Security's Industrial Control Systems Cyber Emergency Response Team (ICS-CERT), sector-specific information sharing and analysis centers (ISACs), the Electric Power Research Institute (EPRI), and CRISP–in the power space has improved markedly, especially concerning actionable information after the 2015 Ukraine grid attack. However, "companies still rarely voluntarily report incident information, and collection of lessons learned is fragmented," the assessment reports.
Meanwhile, though incident reporting is well implemented for the power sector through the North American Electric Reliability Corp.'s critical infrastructure protection standards, the DOE, and E-ISAC requirements, "current processes are driven by compliance more than process improvement, and coordination among reporting mechanisms could be valuable," it says.
Bulk power system participants are apparently also unaware of even the few federally organizations that have originated as a public-private partnership but have become self-sustaining entities. "Few industry members knew of or had engaged with the [National Electric Sector Cybersecurity Organization Resource (NESCOR)]," a self-sustaining entity within the EPRI that brings together domestic and international experts, developers, and users to specify and test security of novel technology, architectures, and applications for the electric sector.
A Long List of Critical To-Dos
Finally, and perhaps of most concern, are a number of continuing industry needs:
Workforce Training and Education. Though several academic entities have stepped up offering new courses and university curricula, "the shortage of qualified cybersecurity professionals remains severe," the assessment says.
Secure Code Development and Software Quality Assurance. "Secure and safe coding practices can be implemented on new products, but high cost, conflicts with legacy products, and lack of demand remain key barriers," it says. The DOE added that to overcome this challenge, significant work will be needed in awareness and workforce training, but it also noted that supply chain risk remains a key issue.
Real-time Security State Monitoring and Risk assessment. Despite the proliferation of a multitude of tools and vendor products for monitoring, "real-time monitoring of OT systems is still a challenge, and no tools can assess new risks in real time."
Secure Serial and Routable Communications and Secure Wireless Communications. Several IT/OT security firms are developing new security protocols and test new approaches on OT systems, however,"implementation across entire systems presents many challenges. Emerging technologies, like SDN, have yet to make a significant impact, the DOE says.
Self-Configuring EDS Network Architectures and Continued Operation During a Cyberattack. Self-configuring and self-defending architectures "largely remain a future state where additional RD&D is needed." The DOE said it continues to support RD&D to develop and transition technologies that adapt operational network pathways to route around disruptions, and technologies that identify compromised power system devices, then adapt to their loss by changing how the remaining, uncompromised devices are used.
Real-time Forensics Capabilities. Also still "largely a black box activity" is forensics for post-event analysis on OT systems. "Large technology gaps remain for conducting forensics and sharing data," it noted. Meanwhile, though new technologies "can automatically identify a cyber incident," substantial RD&D is needed to design systems that can automatically respond or reconfigure to cyber incidents.
Mature Platforms for Information Sharing. According to the DOE, users "find it difficult to keep up with the data and alerts, and need machine-to-machine information sharing to speed response." A better way is needed to allow IT/OT professionals to keep up to date with the daily information dump as it concerns cybersecurity.
–Sonal Patel is a POWER associate editor (@sonalcpatel, @POWERmagazine)
