
Regulatory officials from the European Union Aviation Safety Agency (EASA) and the Federal Aviation Administration (FAA) discussed some of their latest cybersecurity policy initiatives and upcoming regulatory updates during the first day of the Global Connected Aircraft Summit's second "Cabin Chats" web series.
During the first day of the Global Connected Aircraft Summit's second "Cabin Chats" web series, cybersecurity experts from the European Union Aviation Safety Agency (EASA) and the Federal Aviation Administration (FAA) came together to discuss risk management and upcoming policy changes for stakeholders across the connected aircraft ecosystem.
Peter Skaves, Advanced Avionics Chief Scientific and Technical Advisor (CSTA) at FAA, said the biggest threat from the standpoint of the FAA is access points via public networks. The FAA's assessment is that the cybersecurity risks for the e-enabled architecture and infrastructure of the aircraft cannot physically be hacked while flying.
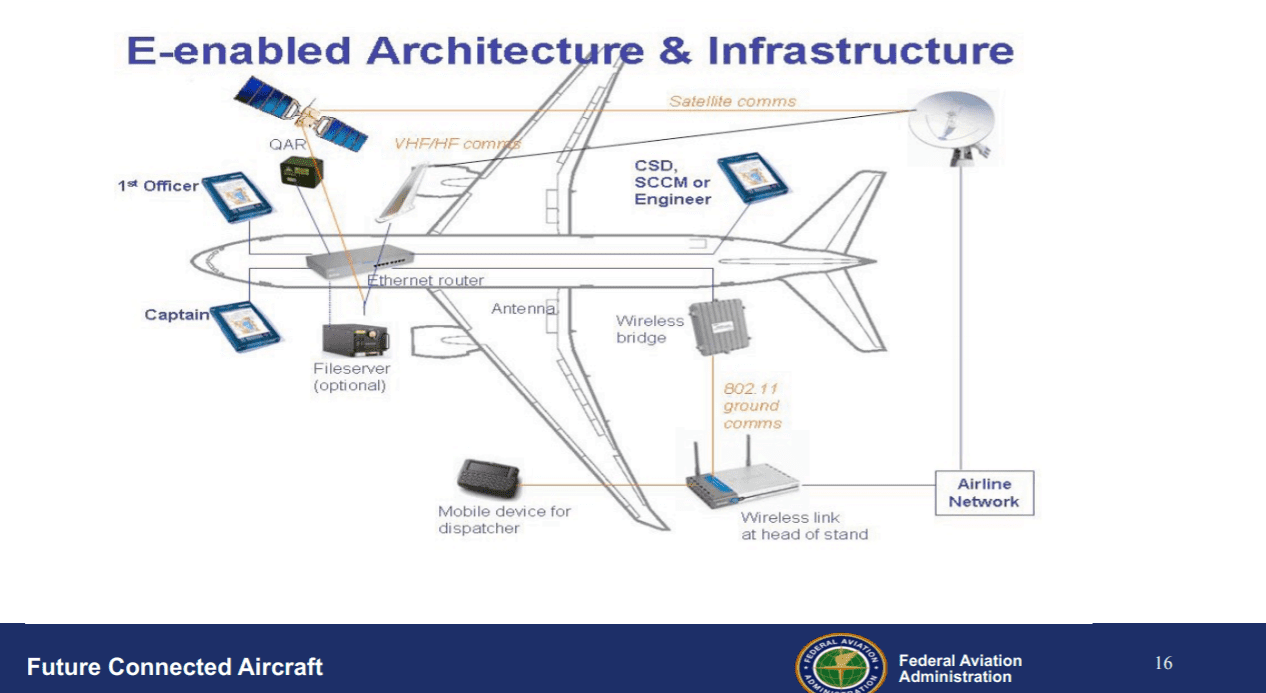
Slide pulled from a presentation by Peter Skaves, Advanced Avionics CSTA at FAA, during the Global Connected Aircraft Summit.
"Every part in the airplane, every software part, has a unique electronic identifier and the only time we can load up these software parts is on a maintenance action when the planes are parked at the gate," Skaves said. "Once the maintenance action is done, the hardware interlocks are not available for any additional software updates. There is no room for you to come over here and go rogue on these displays or anywhere in the airplane. There is no physical way you can do that."
In recent years, professional hackers from firms such as IOACTIVE have demonstrated their ability to hack into a commercial airplane's satellite internet modem, although the only such hacking that has been demonstrated impacted passenger mobile devices connected to the in-flight Internet with no ability to affect safety critical avionics systems. During the web-based version of Black Hat 2020 last month, Oxford PhD candidate and cybersecurity researcher James Pavur, demonstrated how his team was able to use about $300 in home television equipment and specialized software to enable "satellite eavesdropping" on in-flight passenger Internet data.

Slide pulled from a presentation by Peter Skaves, Advanced Avionics CSTA at FAA, at the Global Connected Aircraft Summit.
The FAA and EASA are continuing to expand industry guidance, education and regulations to prevent cybersecurity risks in the air and on the ground.
Cyrille Rosay, a senior cybersecurity expert at EASA, explained how the agency has amended its cybersecurity requirements for commercial aircraft, helicopters, and jet engines. The amendments were originally proposed in 2019. EASA's "Decision 2020/006/R," published in July, issues amendments for product certification and continued airworthiness to already existing certification specifications (CS) and acceptable means of compliance (AMC). These regulations do not yet apply to unmanned aircraft.
Decision 2020/006/R aims to protect aircraft against threats to on-board electronic networks and systems. The amendments in this decision affect everything from general requirements on systems and equipment function in AMC 23.2510 to APU Control Systems and information security protection in CS-APU 90. The new amendments are to become effective in January 2021, according to information presented by Rosay.
Skaves said that the FAA plans to publish an advisory circular to recognize standards for Transport Category Airplanes. The advisory circular will be combined with RTCA industry-accepted standards.
A slide in Skaves presentation noted, "The FAA plans to publish an advisory circular as one means but not the only means to recognize these [Aircraft Systems Information Security/Protection] ASISP industry standards for Transport Category Airplanes."
Juan Anton, cybersecurity in aviation & emerging risks section manager at EASA, discussed how the agency is also working on managing cybersecurity risks by organizations. Anton explained how EASA regulatory framework is focused on preventing accidents, where managing cybersecurity risks focuses on safety risks that result from intentional acts.
"Our rules have always been focused on safety…We put safety layers to stop something from happening, but we assume that it happens just by chance when all things align. We never thought about somebody trying to exploit those vulnerabilities or flaws," Anton said.
Anton said the solution would be an Information Security Management System (ISMS) and reporting of information security incidents that may impact aviation safety. The ISMS would identify areas that would be vulnerable to cyber risks, identify cyber risks resulting from its interfaces with other organizations, perform information security risk assessments, and ensure personnel has the skills to perform their tasks.
EASA is currently working on an ISMS and predicts it will be adopted by the European Commission in 2022.
