While no company wants to envision becoming the victim of a cyberattack, investing time upfront to craft an incident-response plan can provide a quicker path to recovery
Cyberattacks are becoming a way of life – in both our personal, and increasingly, our business lives. The pages of newspapers and trade magazines are full of stories of breaches that have led to the disclosure of personal and financial information. While these attacks can have a devastating effect on the individuals concerned, they cannot be compared to the scope of potential damage caused by security breaches at industrial facilities. With all the media coverage and promptings from cybersecurity vendors, it is impossible not to be aware of the risks. If anything, significant fatigue is beginning to set in as some vendors use fear, uncertainty and doubt to sell their products and services.
According to a survey commissioned by cybersecurity firm Kaspersky Lab (Woburn, Mass.; use.kasperky.com) that quizzed more than 300 professionals with decision-making power on operational-technology (OT) and industrial-control-system (ICS) cybersecurity, 77% of companies believe that cybersecurity is a significant priority [1]. A similar number believe they are likely to become a target of a cyberattack. Despite this raised awareness, only 23% said that they were compliant with minimal mandatory industry or government guidance and regulations around cybersecurity of industrial control systems.
In another report from Ponemon Institute LLC (Traverse City, Mich.; www.ponemon.org), respondents said around half of successful cyberattacks resulted in downtime of critical systems.
Attacks on industrial control systems can potentially cause vast amounts of damage, and in some of the worst cases, explosions. As cyberattacks become more sophisticated, an ICS in particular remains a key target. In the first quarter of 2019, industrial companies ranked second out of organizations most often hit by cyber-attackers globally [ 2].
Chemical operators know they need to manage cybersecurity risk and threats, but they face a number of challenges to do this effectively. In order to master industrial cybersecurity challenges, chemical operators need to develop a robust strategy and put countermeasures into place (Figure 1). They also need to ensure sufficient funding for security programs to run smoothly.
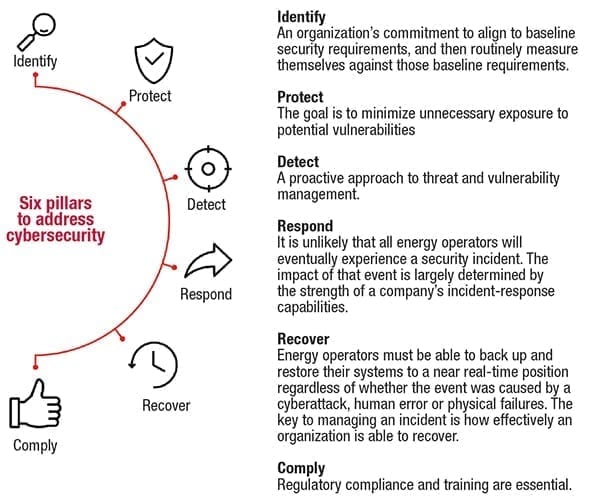
FIGURE 1. This six-pillar approach to cybersecurity focuses not only on incident prevention, but also on crafting an effective response plan in the event that a cyberattack does occur
Proliferation of cloud and edge
There are three main challenges when it comes to securing chemical facilities from cyberattacks. The first is remediating security risks in older systems. Next is developing reference architectures for greenfield sites. Finally come the challenges associated with the proliferation of cloud and edge technologies (Figure 2). Edge devices are those that control data transmission across network boundaries.
Recently, there has been a rapid rise in the use of edge devices and cloud computing, and we need to entirely understand what security means in this context. What controls do we need to implement around different data use cases for cloud and edge technologies? Leading operators in the sector are focusing on the reference architecture as reference use cases in how they would like those security controls designed. However, it is important to recognize that it is not particularly effective to have this reference built in as an afterthought – instead, it needs to be part of the initial system build.

FIGURE 2. The proliferation of cloud and edge connectivity presents new challenges in securing digital and physical assets
CFATS
Unlike many other critical infrastructure sectors, in the U.S., the federal government regulates cybersecurity for the chemical process industries (CPI). Under the Chemical Facility Anti-Terrorism Standards (CFATS), chemical facilities must meet comprehensive cybersecurity requirements that address the protection of business networks and process control systems. See Part 2 of this Feature Report (p. 32) for more information on CFATs.
Beyond CFATS, the chemical sector has also been actively engaged with the federal government as the National Institute of Standards and Technology (NIST; Gaithersburg, MD; www.nist.gov) moves forward with implementing a cybersecurity framework in response to Executive Order 13650, Improving Chemical Facility Safety and Security, in response to the deadly explosion at a fertilizer distribution facility in West, Texas, which occurred in April 2013 [ 3].
This enforcement at a governmental level is great and enables chemical operators – regardless of size, degree of cybersecurity risk or cybersecurity sophistication – to apply the principles and best practices of risk management in improving the security and resilience of their critical infrastructure.
There is not a one-size-fits-all approach, however, in effectively managing cybersecurity risk. Operators will continue to have unique risks – different threats, different vulnerabilities and different risk tolerances – and as such, the impact of a cyber-incident is largely determined by the strength of a company's own incident-response program. Thorough planning and communicating what actions are to be taken and ensuring a coordinated response greatly reduces the potential negative impact.
A chain reaction
When CPI companies begin an investigation after suffering from a cyber-event or cyberattack, one of the first calls usually made is to their digital technology suppliers, asking them to test the system and help the business get back online.
There are significant dependencies put upon suppliers intrinsically linked to internal operations teams. Together, they need to work to answer a number of essential questions after an attack has taken place. For example, are they carrying out system backups frequently enough? Have they undertaken drills, so they know how to recover a system from the ground up? Are they capturing logs that are long enough to provide forensic analysis?
The breadth and depth of this partnership must be agreed upon in advance so that teams can come together seamlessly and quickly to manage damage and limit downtime after an attack.
There is also the outbound supply chain to consider. What is the effect for customers and what damage could limitations, albeit temporary, cause them? These are some of the nuances chemical operators need to understand and have mapped out and ready in the event of an incident.
Responding to a cyber-incident
The three foundations of effective cybersecurity plans are people, process and technology. Many organizational policies focus on the latter two factors, but people are just as critical to maintaining a robust security posture (Figure 3).

FIGURE 3. Educating all personnel in their role and stake in cybersecurity-related matters is a critical pillar in maintaining secure facilities
With these principles in mind, the pathway to overcoming a cyberattack on an industrial control system follows a multi-step process of appraisal, understanding and action, which is detailed in the following sections.
Step 1. Establish communication and partnerships. First, begin by understanding the internal partnerships and relationships that are needed to achieve industry response resilience. The challenge arises because a cyber-incident could threaten any component, piece of equipment or process across an entire business. Establishing communication and complete visualizations of operations and how different elements partner or relate to one another is vital to success. As mentioned previously, these interactions are complex and can involve many pieces of the supply chain.
Step 2. Design incident-response drills.It is crucial to not overlook the importance of designing incident-response drills to expose potential gaps and friction points in the process. When it comes to responding to a cyber-event, all interactions, responsibilities and interdependencies are crucial. It cannot be emphasized enough how vital recovery drills and effective scenario playbooks are to foster understanding and compliance. For example, a drill could be that the team can run through specific scenarios.
Incident-response drilling is essential, because it not only helps understand potential scenarios, but it also improves the elasticity of a security team and its procedures. Can they adapt to change well? Can they work well together? Does leadership understand how to act when there is a security event?
Gaining insight and knowledge into what is required, both from a procedural and a culture standpoint, is extremely beneficial. It is like the analogy of forcing water through a pipe – you want to know where the leaks are when you are carrying out drills, not when it is a real incident.
Step 3. Develop and track KPIs.Focused tracking of key performance indicators (KPIs) around incident responses leads to a better understanding of risk, investment needs and opportunities to improve. There can be a serious gap here with leadership understanding when it pertains to cybersecurity. It is commonly seen that the only time leaders hear about their security teams and the excellent work they do is when there is an incident, or when there is an issue around availability – then, it is rarely positive. These teams work ceaselessly to defend the plant and processes, to improve the overall recovery time, or improve on their drills. Responsibility for managing risk must start with leaders – board members and chief executives need to lead a top-down approach in developing a culture of cyber-resilience.
The ability to have a discussion of cybersecurity with leadership and to get them to build confidence in the subject is crucial. Leadership responses can also be critical in positioning how a company is perceived externally. This is an area with which leadership needs to get comfortable handling and managing competently.
Step 4. Assemble the team.Though reasonably simple, having strong incident-response policies and procedures in place, backed with reliable enforcement, cannot just be driven by a security team. These procedures need to be understood and followed by all relevant stakeholders in a company, from operations through to the legal and communications departments, to make sure that they are practical, and that team members can implement them effectively.
Step 5. Create a playbook. This step is traditionally called operating models, but a better name might be incident-response playbooks. The key here is that these playbooks are living constructs, and they reflect the inputs of the stakeholders that would be engaged in an incident. Playbooks are the basis for action, and they give team members boundaries. More importantly, they allow flexibility to improve and work effectively, which is crucial because cybersecurity is not static.
Step 6. Consider stakeholders. Last but not least, remember relevant stakeholders. One thing to always emphasize is the importance of open communication. Many companies suffer from adverse press coverage around security events if they do not communicate transparently and in a timely manner about what is going on.
While it might not help in immediately restoring operations, having robust communications engagement will certainly deliver longterm benefits. Having a strong communication plan in place helps customers and all impacted parties to be more comfortable in the event of a cyber-incident.
Right now, many operators are even employing agencies that specialize in security-incident-response communications, which can craft holding statements to inform and soothe the sentiments of all stakeholders. This transparent and upfront approach can be critical in impacting share price, goodwill and company perceptions.
Ensuring a resilient response
The vital element in all of this is building security elasticity into the chemical organization. Over the past ten years, we have heard a lot –some would say too much – about OT security. We have heard about minimum standards, about the do's and the don'ts. We have heard so much about this that there is now a reference to "basic cybersecurity hygiene." However, this phrase implies that many cybersecurity challenges might have been avoidable, had a higher level of diligence been applied. The flipside of this coin, in contrast, is providing resiliency in incident response.
While the focus to be "secure-by-design" is excellent and necessary, as an industry, we now have a unique opportunity to focus a bit more on incident response. By doing this, we can ensure that our resiliency lines up precisely with our enterprise risk-management principles.
The best way to mitigate cyber-risk or to recover quickly after an attack is to embed the principles of identification, protection, detection, response, recovery and compliance within organizational behavior and culture, and apply best-practice learnings from system design through to the decommissioning stages of critical process equipment.
It is vital to remember that even though it is challenging to find the time for both security and operations teams, any time spent upfront on incident response is going to help chemical operators be more resilient. Waiting until an incident occurs to learn about incident response is not recommended. Instead, the smartest CPI operators are preparing for tomorrow by investing today. This wiser decision will support their resiliency and performance in the longterm. ■
Edited by Mary Page Bailey
References
1. PAC on behalf of Kaspersky Lab, The State of (Global)Industrial Cybersecurity 2018; ics.kaspersky.com/the-state-of-industrial-cybersecurity-2018/.
2. Positive Technologies, Cybersecurity Threatscape Q1 2019, June 2019, www.ptsecurity.com/ww-en/analytics/cybersecurity-threatscape-2019-q1/.
3. U.S. Environmental Protection Agency, Executive Order on Improving Chemical Facility Safety and Security, August 1, 2013, www.epa.gov/rmp/executive-order-improving-chemical-facility-safety-and-security.
Author
 Zied M. Ouertani is the global technology manager, Chemicals and Refining, Energy Industries at ABB (Phone: +49 6213811012; Email: mohamed-zied.ouertani@de.abb.com). Located in Mannheim, Germany, Ouertani joined ABB in 2012 and has served as the company's principal scientist in corporate research and as a business consultant for corporate strategy. He holds a PhD in information systems. He brings more than 10 years of global experience, and is skilled at connecting customer needs to value-added digital solutions. Prior to ABB, he worked at the University of Cambridge, U.K., as a postdoctoral researcher for the Cambridge Service Alliance, and as a business transformation consultant for IBM, BAE Systems and Caterpillar.
Zied M. Ouertani is the global technology manager, Chemicals and Refining, Energy Industries at ABB (Phone: +49 6213811012; Email: mohamed-zied.ouertani@de.abb.com). Located in Mannheim, Germany, Ouertani joined ABB in 2012 and has served as the company's principal scientist in corporate research and as a business consultant for corporate strategy. He holds a PhD in information systems. He brings more than 10 years of global experience, and is skilled at connecting customer needs to value-added digital solutions. Prior to ABB, he worked at the University of Cambridge, U.K., as a postdoctoral researcher for the Cambridge Service Alliance, and as a business transformation consultant for IBM, BAE Systems and Caterpillar.
