The North American Electric Reliability Corp. (NERC) standard on physical security–known as Critical Infrastructure Protection-014 (CIP-014)–includes six basic requirements, but perhaps the most challenging for power companies is to develop and implement a documented physical security plan. Tower-mounted robotics powered by artificial intelligence could make that easier.
The U.S. power grid is wide open for attack. More than 200,000 miles of high-voltage transmission lines, interspersed with hundreds of large electric power transformers and substations span the country, often in remote locations. In response to growing threats, NERC issued requirements for the physical security of critical transmission stations and substations, and their associated primary control centers. Meeting these mandates is costly and complicated for utility owners and operators. Fortunately, new advancements in technology–particularly in the fields of robotics and artificial intelligence–can offer proactive protection against attackers at a reasonable cost and help utilities achieve compliance.
Power Grid Vulnerability
An attack on the power grid can cause significant damage. In fact, the loss of only nine substations could take down the nation's entire grid, according to one study. Paul Parfomak, a specialist in energy and infrastructure policy, noted in a congressional report, "Experts have long asserted that a coordinated and simultaneous attack on multiple high-voltage transformers could have severe implications for reliable electric service over a large geographic area, crippling its electricity network and causing widespread, extended blackouts. Such an event would have serious economic and social consequences."
Especially vulnerable to attack are what one former Navy SEAL and U.S. intelligence officer called soft targets. "These are generally remote areas that just have a fence around them, maybe a camera system … they're not hard at all to actually take down," he said in a recent interview. He added, "For a small handful of people to take down a power grid, it's just not that hard … this is absolutely one of the easiest possible things you can do to drive urban areas into total chaos."
The NERC regulations–known as CIP-014–include six basic requirements, such as a risk assessment to identify critical facilities, independent verification of the risk assessment, and evaluation of the potential threats and vulnerabilities of a physical attack on these critical stations or substations. Perhaps the most challenging requirement is to develop and implement a documented physical security plan. According to the directive, this plan must have the following elements:
- Resiliency or security measures designed collectively to deter, detect, delay, assess, communicate, and respond to potential physical threats and vulnerabilities identified during the evaluation.
- Law enforcement contact and coordination information.
- A timeline for executing the physical security enhancements and modifications specified in the physical security plan.
- Provisions to evaluate evolving physical threats, and their corresponding security measures.
Challenges to Compliance
Utility owners and operators face several barriers to CIP-014 compliance. The biggest one is cost. Traditionally, security has not been viewed as a sensible investment. A 2006 report from the Electric Power Research Institute noted: "Security measures, in themselves, are cost items, with no direct monetary return. The benefits are in the avoided costs of potential attacks whose probability is generally not known. This makes cost-justification very difficult."
A related concern is the quality of threat information provided by the federal government and other sources. This information determines what needs to be protected against and what security measures to take. As Parfomak wrote, "Incomplete or ambiguous threat information–especially from the federal government–may lead to inconsistency in physical security among grid owners, inefficient spending of limited security resources at facilities (e.g., that may not really be under threat), or deployment of security measures against the wrong threat."
Artificial Intelligence Offers Real-World Protection
Meeting CIP-014 requirements takes careful planning and wise use of limited resources. Ballistic walls around the perimeters of critical substations are not effective, and hiring a full-time guard force–whether armed or not–is simply not feasible, particularly for remote substations in sparsely populated areas. A more-reasonable, more-effective approach to fences and firearms is the use of advanced technology.
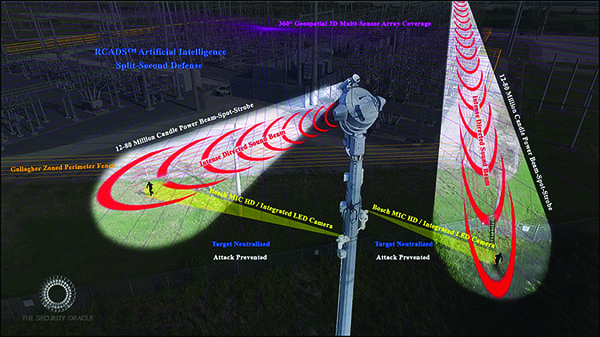
Among the more innovative solutions are tower-mounted robots powered by artificial intelligence (AI). Such technology connected to a high-speed network could transform a power grid's passive security system into an active defense-and-denial physical protection system. Using non-lethal actuators, such as cameras and sensors, the system detects, delays, and safely thwarts a potential attacker by overwhelming them with directed, high-intensity sound, lights, and strobes. Figure 1 illustrates how the system delivers these defense mechanisms to neutralize a target.
In addition, such a system would deliver actionable intelligence in real time to law enforcement, so officers can respond appropriately and effectively. The use of AI-driven robotics technology provides affordable, advanced protection 24/7.
Overcoming Complexity
An AI-driven robotics system typically requires equipment from many different vendors, as no single vendor makes all the equipment necessary to meet more advanced requirements, including an advanced computing infrastructure linked to central offices. Examples of different types of equipment include network routers, satellite antennas/modems, wireless base stations/access points, servers, and firewalls. To avoid long technical learning curves, along with complex setup and maintenance procedures, this equipment should adhere to corporate standards as much as possible.
Most corporate environments are already based upon standard networking equipment from industry leaders such as Cisco Systems, Brocade, Hewlett Packard Enterprise (HPE), and others. It is preferable for deployed networking equipment at remote stations or substations to be easily incorporated into the existing corporate standard network. Unfortunately, commercial off-the-shelf (COTS) equipment intended for office environments is not sufficiently ruggedized for supporting remote locations where they can face challenges like extreme heat and cold. This puts utilities in the uncomfortable position of either looking for specialized equipment that can handle harsh environments, or hoping that the COTS equipment will survive. To enable a 24/7 active defense system, a reliable network and communications infrastructure is vital.
Beyond security, adding networking infrastructure to substations allows organizations to successfully adopt new technology that can improve reliability and reduce unscheduled downtime by protecting electrical equipment in new and better ways. For example, new condition monitoring systems based on internet of things (IoT) technologies can be used for thermal switchgear supervision. This monitoring information can also be used by asset management tools to optimize investments and reduce maintenance costs by moving from time-based maintenance to condition-based maintenance schemes.
Evaluating Ruggedized Equipment
While power companies undeniably must deal with harsh conditions, the gold standard for dealing with challenging conditions is the U.S. military, which has moved away from the use of custom networking gear toward the adoption of ruggedized COTS-based technologies. Such technology is now being adopted in commercial organizations for a range of IoT, video monitoring, and communications applications at the network's edge.
Based on components tested by military standards, the preferred hardware performs in the harshest and most-extreme environments, and typically includes power conditioning and uninterruptible power supply (UPS) systems. While office-grade equipment can be paired with UPS systems, this adds additional expense and creates another layer of complexity. Along these same lines, sophisticated military-grade components do not require environmental conditioning, so there is no need for data-center-style air conditioning.
Ruggedized COTS equipment intended for military applications is typically much more compact than standard rack-mounted office equipment. With its small form factor design and other chassis enclosure options, modern ruggedized networking equipment is much easier to move from location to location. Today, compact, ruggedized, high-performance virtualization platforms for hosting multiple software applications have been adapted for commercial applications.
Another bonus to working with vendors with military experience is the potential for increased security from attacks of all sorts. Based on technologies approved by the U.S. National Security Agency and the U.S. Department of Defense, military-grade equipment can secure the most sensitive industrial networks, thus ensuring the availability, integrity, and confidentiality of data and control. For power stations that are vulnerable to physical attack–and for operators who must comply with NERC CIP-014 standards–security is of utmost priority and must be rigorously maintained. It is comforting to know that new, resilient technologies, including artificial intelligence-driven robots, are already significantly bolstering transmission substation defenses. ■
–Steve Bowen is senior commercial business development manager at PacStar. Charles Butler is CEO of The Security Oracle. Samuel M. Smith, PhD is founder and principal engineer at ProSapien LLC.